API keys
Ensure Data Security with Unique Identifiers.
What is API key?
API keys are the unique identifiers mainly utilised for authorised requests. They function as the so-called bridge between the application and the API and act as digital passwords for any type of sensitive data. In such a respect, API keys can be linked to particular accounts with a complete set of limited permissions to prevent data-related issues.
The API keys help to limit and restrict unauthorised access to data and greatly influence security control and implementation.
The benefits of data encryption with API keys
1. Access to restricted data
Storing sensitive data is a great challenge. There may appear numerous cases when the data can be lost or transmitted to unverified individuals who may use it illegally. Thus, it is crucial to add an additional layer of security to prevent such cases and work with the most appropriate and risk-free methods of PII and data handling. Thus, storing the API keys to data is much easier and safer than gathering raw data on devices.
2. Data control and risk prevention
The data access that is performed via the API keys is more likely to be secure as the control is better managed and established. The Key can be revoked as soon as any suspicious activity is detected without affecting other users.
3. Usage monitoring
Monitoring is another vital component when opting for API key usage. The system where the Keys are stored should allow you to track the Key history and review who has access to a particular Key. It reduces the amount of atypical access attempts and eliminates the number of risks involved in Key management.
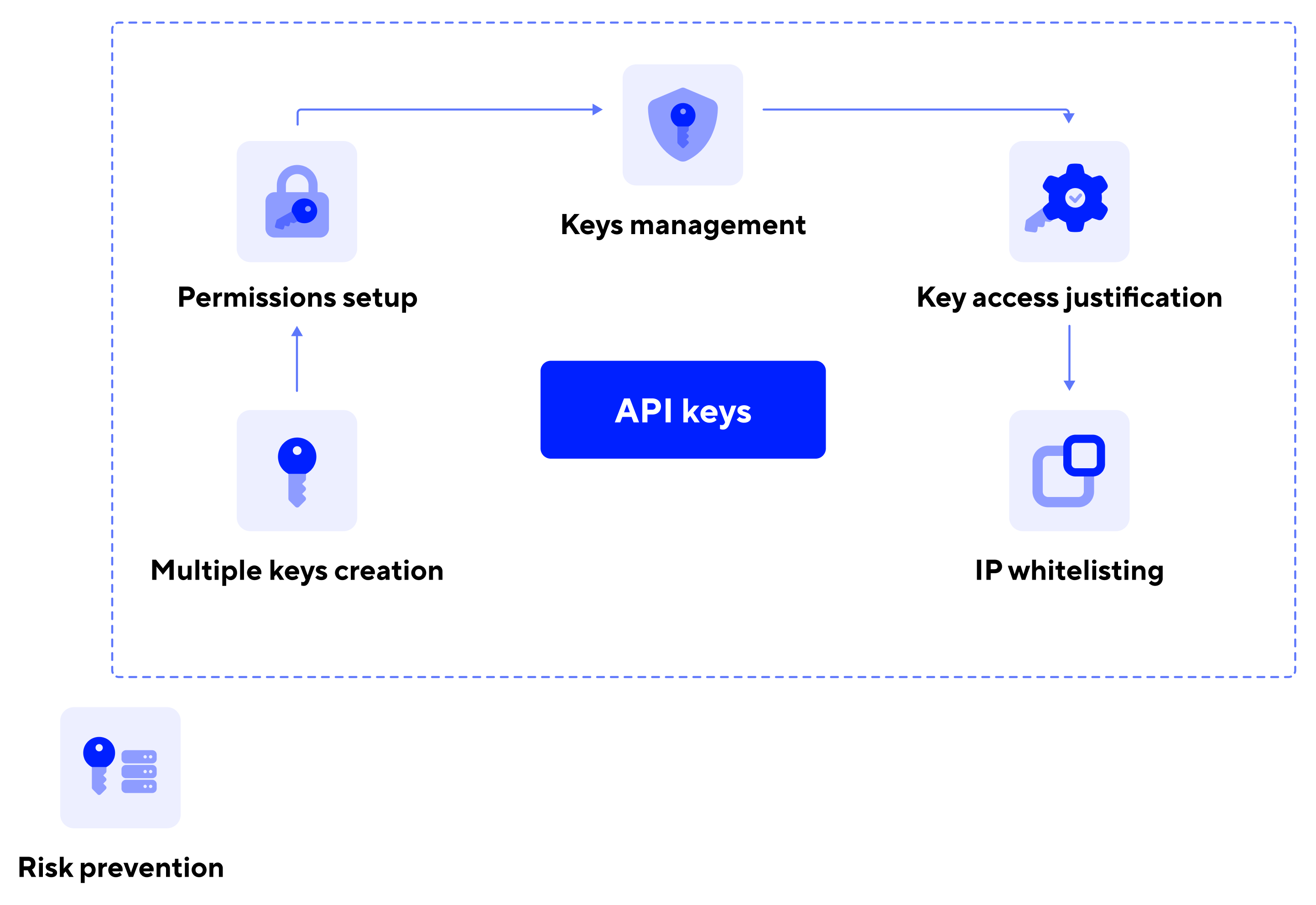
API keys usage – Corefy best practices
You can create several Keys to match your needs. The flow is relatively simple as the system provides you with the corresponding fields where you can enter the appropriate values. You can manage those Keys later if any changes are supposed to come up.
The permissions setup is tremendously important in the process of creating the Keys. You can establish the relevant restrictions and access limits only once; there is no possibility of altering those settings afterwards. Such a policy is implemented for security reasons and to increase access control.
IP whitelisting is simple yet effective in terms of data access management. Therefore, we provide you with the option to create a list of IPs that should be detected as compatible with our system. The requests made from those chosen IPs can be considered as safe. Such a feature can reinforce the security potential and initially eliminate additional risks.
It is crucial for Merchants to use straightforward integration methods and reduce the time and cost of manual implementations. That is where the API keys come in handy and enable smooth integration and refined payment experiences for Customers.
We strongly cherish the idea that security should be among the top priorities and we adhere to PSI DSS Compliance. Our platform provides Merchants with the API key-based services that are aligned with PSI DSS requirements.
Using the API keys, Merchants can automate a lot of manual processes in the payment workflow. In turn, automated procedures can significantly reduce potential errors and save time. Our platform allows strong practices of simplified process automation.
Updated 3 months ago
